About Us
We monitor your I.T system and data assets on premises or on cloud, in real-time to detect vulnerabilities, threats, intrusions, and behavioral anomalies.
We identify misconfigurations and vulnerabilities in your I.T system and applications, and remediate them, providing a secure and resilent I.T system and adherence to regulatory compliance.
We also provide threat intelligence by looking for malware, rootkits, file changes, and suspicious anomalies to detect hidden files, cloaked processors, unregistered network listeners, and inconsistencies in system call responses.
Security Log Analysis
We protect your I.T infrastructure and meet regulatory compliance by monitoring and auditing endpoint activity.
Security Configuration Assessment
We scan your system against the Center for Internet Security (CIS) benchmark and remediate vulnerabilities, misconfigurations, or deviations from best practices and security standards.

Regulatory Compliance
We track and demonstrate compliance with various regulatory frameworks such as PCI DSS, NIST 800-53, GDPR, and HIPAA.
Vulnerability Detection
We detect and prioritize vulnerabilities, ensuring you meet regulatory compliance requirements while reducing your attack surface
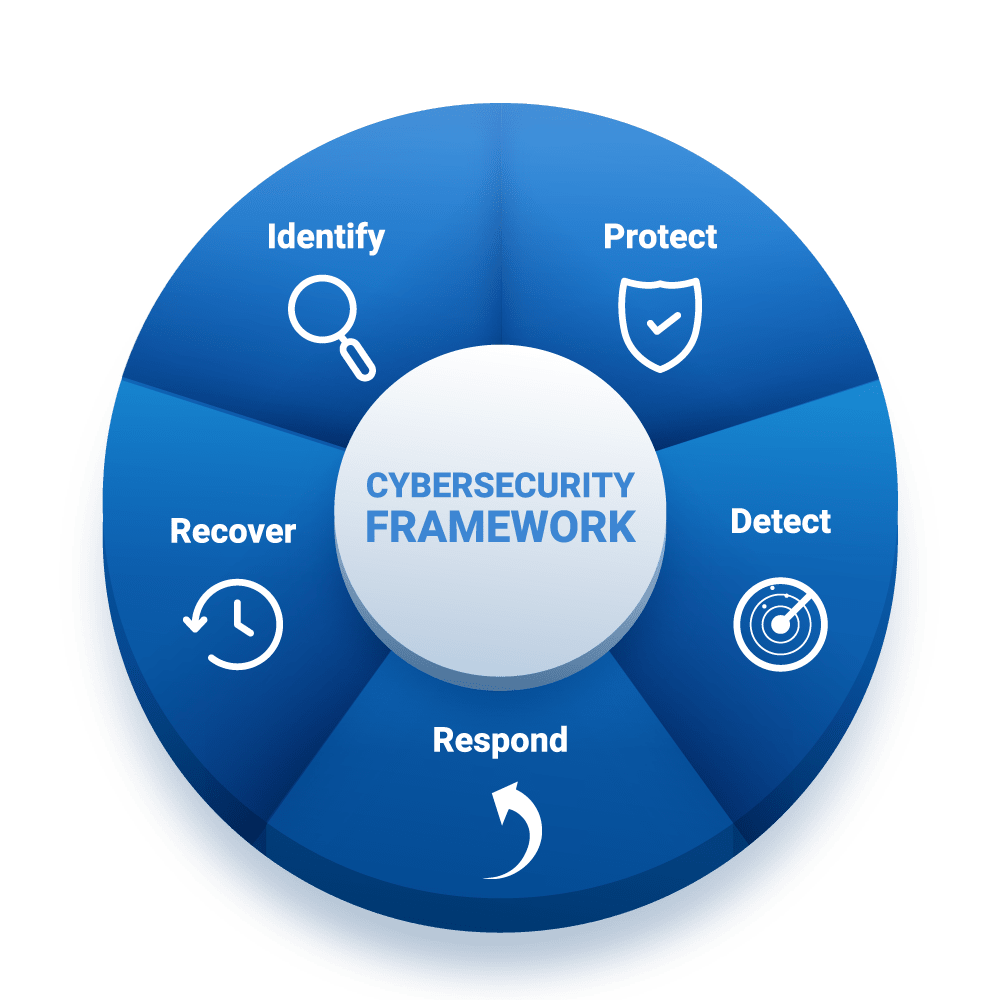
Approach
Our Approach to Security & Prevention
With advanced threat hunting capabilities, we take a proactive approach in identifying and eliminating emerging threats.
We use threat intelligence platforms like VirusTotal, AlienVault OTX, and AbuseIPDB to harness the latest threat intelligence data, empowering us to identify potential threats and conduct thorough investigations.
Contact Us
contact@cyberon.co.za
South Africa
Get Started
Secure your data assets today and become hacker-proof
